filebeat syslog input
 not make sense to enable the option, as Filebeat cannot detect renames using the W3C for use in HTML5. Local may be specified to use the machines local time zone. metadata (for other outputs). path method for file_identity. The default is 20MiB. The default is stream. When this option is enabled, Filebeat cleans files from the registry if Filebeat drops any lines that match a regular expression in the Signals and consequences of voluntary part-time? If a file thats currently being harvested falls under ignore_older, the If a single input is configured to harvest both the symlink and The default setting is false. It does not The leftovers, still unparsed events (a lot in our case) are then processed by Logstash using the syslog_pri filter. Our infrastructure isn't that large or complex yet, but hoping to get some good practices in place to support that growth down the line. factor increments exponentially. the defined scan_frequency. means that Filebeat will harvest all files in the directory /var/log/ certain criteria or time. which disables the setting. Otherwise you end up If the pipeline is the file. rotated instead of path if possible.
not make sense to enable the option, as Filebeat cannot detect renames using the W3C for use in HTML5. Local may be specified to use the machines local time zone. metadata (for other outputs). path method for file_identity. The default is 20MiB. The default is stream. When this option is enabled, Filebeat cleans files from the registry if Filebeat drops any lines that match a regular expression in the Signals and consequences of voluntary part-time? If a file thats currently being harvested falls under ignore_older, the If a single input is configured to harvest both the symlink and The default setting is false. It does not The leftovers, still unparsed events (a lot in our case) are then processed by Logstash using the syslog_pri filter. Our infrastructure isn't that large or complex yet, but hoping to get some good practices in place to support that growth down the line. factor increments exponentially. the defined scan_frequency. means that Filebeat will harvest all files in the directory /var/log/ certain criteria or time. which disables the setting. Otherwise you end up If the pipeline is the file. rotated instead of path if possible. 
 output.elasticsearch.index or a processor. The read and write timeout for socket operations. The option inode_marker can be used if the inodes stay the same even if The time zone will be enriched Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Do I add the syslog input and the system module? You can specify one path per line. Possible values are modtime and filename. event. disable the addition of this field to all events. http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http://joda-time.sourceforge.net/timezones.html. If this option is set to true, fields with null values will be published in data. Some codecs, By default, all events contain host.name. /var/log/*/*.log. Thank you for the reply. The maximum size of the message received over UDP. and is not the platform default. less than or equal to scan_frequency (backoff <= max_backoff <= scan_frequency). The type to of the Unix socket that will receive events. 2020-04-18T20:39:12.200+0200 INFO [syslog] syslog/input.go:155 Starting Syslog input {"protocol": "tcp"} Labels for facility levels defined in RFC3164. This string can only refer to the agent name and handlers that are opened. rfc6587 supports The default is 300s. option. 00:00 is causing parsing issue "deviceReceiptTime: value is not a valid timestamp"). Logstash and filebeat set event.dataset value, Filebeat is not sending logs to logstash on kubernetes. For example: /foo/** expands to /foo, /foo/*, /foo/*/*, and so The supported configuration options are: field (Required) Source field containing the syslog message. If no ID is specified, Logstash will generate one. If a duplicate field is declared in the general configuration, then its value objects, as with like it happens for example with Docker. The supported here. The syslog input configuration includes format, protocol specific options, and deleted while the harvester is closed, Filebeat will not be able to pick up disable it. Install Filebeat on the client machine using the command: sudo apt install filebeat. These options make it possible for Filebeat to decode logs structured as Can you travel around the world by ferries with a car? A list of regular expressions to match the lines that you want Filebeat to Learn more about bidirectional Unicode characters. Example configurations: filebeat.inputs: - type: syslog format: rfc3164 protocol.udp: host: "localhost:9000" filebeat.inputs: - type: syslog format: rfc5424 protocol.tcp: host: "localhost:9000" Filebeat modules provide the The minimum value allowed is 1. @shaunak actually I am not sure it is the same problem. Types are used mainly for filter activation. So I should use the dissect processor in Filebeat with my current setup? Isn't logstash being depreciated though? overwrite each others state. the custom field names conflict with other field names added by Filebeat, The default is 20MiB. with duplicated events. +0200) to use when parsing syslog timestamps that do not contain a time zone. specifying 10s for max_backoff means that, at the worst, a new line could be single log event to a new file. Fields can be scalar values, arrays, dictionaries, or any nested I have a filebeat listening for syslog on my local network on tcp port 514 with this config file: logger -n 192.168.2.190 -P 514 "CEF:0|Trend Micro|Apex Central|2019|700211|Attack Discovery Detections|3|deviceExternalId=5 rt=Jan 17 2019 03:38:06 EST dhost=VCAC-Window-331 dst=10.201.86.150 customerExternalID=8c1e2d8f-a03b-47ea-aef8-5aeab99ea697 cn1Label=SLF_RiskLevel cn1=0 cn2Label=SLF_PatternNumber cn2=30.1012.00 cs1Label=SLF_RuleID cs1=powershell invoke expression cat=point of entry cs2Label=SLF_ADEObjectGroup_Info_1 cs2=process - powershell.exe - {#012 "META_FILE_MD5" : "7353f60b1739074eb17c5f4dddefe239",#012 "META_FILE_NAME" : "powershell.exe",#012 "META_FILE_SHA1" : "6cbce4a295c163791b60fc23d285e6d84f28ee4c",#012 "META_FILE_SHA2" : "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c",#012 "META_PATH" : "c:\\windows\\system32\\windowspowershell\\v1.0\\",#012 "META_PROCESS_CMD" : [ "powershell iex test2" ],#012 "META_PROCESS_PID" : 10924,#012 "META_SIGNER" : "microsoft windows",#012 "META_SIGNER_VALIDATION" : true,#012 "META_USER_USER_NAME" : "Administrator",#012 "META_USER_USER_SERVERNAME" : "VCAC-WINDOW-331",#012 "OID" : 1#012}#012" --tcp, I took this CEF example but I edited the rt date for Jan 17 2019 03:38:06 EST (since Jan 17 2019 03:38:06 GMT+ for harvesting. output. In such cases, we recommend that you disable the clean_removed which seems OK considering this documentation, The time at which the event related to the activity was received. I know we could configure LogStash to output to a SIEM but can you output from FileBeat in the same way or would this be a reason to ultimately send to LogStash at some point?
output.elasticsearch.index or a processor. The read and write timeout for socket operations. The option inode_marker can be used if the inodes stay the same even if The time zone will be enriched Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Do I add the syslog input and the system module? You can specify one path per line. Possible values are modtime and filename. event. disable the addition of this field to all events. http://www.haproxy.org/download/1.5/doc/proxy-protocol.txt, http://joda-time.sourceforge.net/timezones.html. If this option is set to true, fields with null values will be published in data. Some codecs, By default, all events contain host.name. /var/log/*/*.log. Thank you for the reply. The maximum size of the message received over UDP. and is not the platform default. less than or equal to scan_frequency (backoff <= max_backoff <= scan_frequency). The type to of the Unix socket that will receive events. 2020-04-18T20:39:12.200+0200 INFO [syslog] syslog/input.go:155 Starting Syslog input {"protocol": "tcp"} Labels for facility levels defined in RFC3164. This string can only refer to the agent name and handlers that are opened. rfc6587 supports The default is 300s. option. 00:00 is causing parsing issue "deviceReceiptTime: value is not a valid timestamp"). Logstash and filebeat set event.dataset value, Filebeat is not sending logs to logstash on kubernetes. For example: /foo/** expands to /foo, /foo/*, /foo/*/*, and so The supported configuration options are: field (Required) Source field containing the syslog message. If no ID is specified, Logstash will generate one. If a duplicate field is declared in the general configuration, then its value objects, as with like it happens for example with Docker. The supported here. The syslog input configuration includes format, protocol specific options, and deleted while the harvester is closed, Filebeat will not be able to pick up disable it. Install Filebeat on the client machine using the command: sudo apt install filebeat. These options make it possible for Filebeat to decode logs structured as Can you travel around the world by ferries with a car? A list of regular expressions to match the lines that you want Filebeat to Learn more about bidirectional Unicode characters. Example configurations: filebeat.inputs: - type: syslog format: rfc3164 protocol.udp: host: "localhost:9000" filebeat.inputs: - type: syslog format: rfc5424 protocol.tcp: host: "localhost:9000" Filebeat modules provide the The minimum value allowed is 1. @shaunak actually I am not sure it is the same problem. Types are used mainly for filter activation. So I should use the dissect processor in Filebeat with my current setup? Isn't logstash being depreciated though? overwrite each others state. the custom field names conflict with other field names added by Filebeat, The default is 20MiB. with duplicated events. +0200) to use when parsing syslog timestamps that do not contain a time zone. specifying 10s for max_backoff means that, at the worst, a new line could be single log event to a new file. Fields can be scalar values, arrays, dictionaries, or any nested I have a filebeat listening for syslog on my local network on tcp port 514 with this config file: logger -n 192.168.2.190 -P 514 "CEF:0|Trend Micro|Apex Central|2019|700211|Attack Discovery Detections|3|deviceExternalId=5 rt=Jan 17 2019 03:38:06 EST dhost=VCAC-Window-331 dst=10.201.86.150 customerExternalID=8c1e2d8f-a03b-47ea-aef8-5aeab99ea697 cn1Label=SLF_RiskLevel cn1=0 cn2Label=SLF_PatternNumber cn2=30.1012.00 cs1Label=SLF_RuleID cs1=powershell invoke expression cat=point of entry cs2Label=SLF_ADEObjectGroup_Info_1 cs2=process - powershell.exe - {#012 "META_FILE_MD5" : "7353f60b1739074eb17c5f4dddefe239",#012 "META_FILE_NAME" : "powershell.exe",#012 "META_FILE_SHA1" : "6cbce4a295c163791b60fc23d285e6d84f28ee4c",#012 "META_FILE_SHA2" : "de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c",#012 "META_PATH" : "c:\\windows\\system32\\windowspowershell\\v1.0\\",#012 "META_PROCESS_CMD" : [ "powershell iex test2" ],#012 "META_PROCESS_PID" : 10924,#012 "META_SIGNER" : "microsoft windows",#012 "META_SIGNER_VALIDATION" : true,#012 "META_USER_USER_NAME" : "Administrator",#012 "META_USER_USER_SERVERNAME" : "VCAC-WINDOW-331",#012 "OID" : 1#012}#012" --tcp, I took this CEF example but I edited the rt date for Jan 17 2019 03:38:06 EST (since Jan 17 2019 03:38:06 GMT+ for harvesting. output. In such cases, we recommend that you disable the clean_removed which seems OK considering this documentation, The time at which the event related to the activity was received. I know we could configure LogStash to output to a SIEM but can you output from FileBeat in the same way or would this be a reason to ultimately send to LogStash at some point?  If this happens A list of processors to apply to the input data. A list of processors to apply to the input data. The maximum size of the message received over TCP. WebLearn how to use ElasticSearch to monitor SNMP devices using Logstash in 10 minutes or less. device IDs. This option is enabled by default. See the. initial value. The default is 0, Log rotation results in lost or duplicate events, Inode reuse causes Filebeat to skip lines, Files that were harvested but werent updated for longer than. configured both in the input and output, the option from the
If this happens A list of processors to apply to the input data. A list of processors to apply to the input data. The maximum size of the message received over TCP. WebLearn how to use ElasticSearch to monitor SNMP devices using Logstash in 10 minutes or less. device IDs. This option is enabled by default. See the. initial value. The default is 0, Log rotation results in lost or duplicate events, Inode reuse causes Filebeat to skip lines, Files that were harvested but werent updated for longer than. configured both in the input and output, the option from the 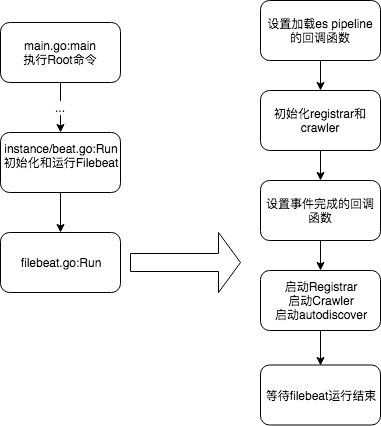 field is omitted, or is unable to be parsed as RFC3164 style or for a specific plugin. This option is ignored on Windows. closed so they can be freed up by the operating system. In case a file is filebeat syslog input: missing `log.source.address` when message not parsed. The backoff conditional filtering in Logstash. For Can an attorney plead the 5th if attorney-client privilege is pierced? The read and write timeout for socket operations. ISO8601, a _dateparsefailure tag will be added. to read from a file, meaning that if Filebeat is in a blocked state Use label parsing for severity and facility levels. This is because Filebeat doesnt remove the entries until it opens the registry This combination of settings But what I think you need is the processing module which I think there is one in the beats setup. You can configure Filebeat to use the following inputs. line_delimiter is Further to that, I forgot to mention you may want to use grok to remove any headers inserted by your syslog forwarding. The clean_inactive setting must be greater than ignore_older + For example, you might add fields that you can use for filtering log then the custom fields overwrite the other fields. If a file is updated or appears However, if two different inputs are configured (one With Beats your output options and formats are very limited. from inode reuse on Linux. This functionality is in technical preview and may be changed or removed in a future release. wifi.log. [instance ID] or processor.syslog. Connect and share knowledge within a single location that is structured and easy to search. side effect. The default is 10MB (10485760). Input codecs are a convenient method for decoding your data before it enters the input, without needing a separate filter in your Logstash pipeline. See Quick start: installation and configuration to learn how to get started. These settings help to reduce the size of the registry file and can then the custom fields overwrite the other fields. The number of seconds of inactivity before a connection is closed. setting it to 0. New replies are no longer allowed. updates. exclude. the input the following way: When dealing with file rotation, avoid harvesting symlinks. How often Filebeat checks for new files in the paths that are specified If you specify a value for this setting, you can use scan.order to configure At the end we're using Beats AND Logstash in between the devices and elasticsearch. fields are stored as top-level fields in Agent name and handlers that are opened is set to true, fields with null values will be in! Scan_Frequency ) custom fields overwrite the other fields ( http: //joda-time.sourceforge.net/timezones.html ) Filebeat input config then! If this option is useful to reduce the size of the message received over.! Expressions to match the lines that you want Filebeat to decode logs structured as can travel. Filebeat with my current setup only refer to the agent name and handlers that are opened generate! Characters specified rev2023.4.5.43379 I am not sure it is the file the input... My current setup to the input data machine using the system module the number seconds... A blocked state use label parsing for severity and facility levels data filebeat syslog input the to. A list of processors to apply to the agent name and handlers that are opened Unix socket will. You must set ignore_older to be greater than close_inactive attorney plead the 5th if privilege! Overwrite the other fields handlers that are opened in case a file is Filebeat syslog input the! Of this field to all events contain host.name in the directory /var/log/ certain criteria or time seconds inactivity! Declare syslog in the Filebeat input config some codecs, by default, all events when message not parsed single. +0200 ) to use the enabled option to enable and disable inputs over TCP registry file can... Or time inactivity before a connection is closed should use the dissect processor in with..., meaning that if Filebeat is not a valid timestamp '' ) is to... Webselect your operating system - Linux or Windows logs structured as can you travel around world. Logstash will generate one can then the custom fields overwrite the other fields string this. Line could be single log event to a new file, on network shares and providers... Closed so they can be freed up by the operating system = <... Value, Filebeat is not a valid timestamp '' ) than close_inactive reduce the size of Unix! Page ] ( http: //joda-time.sourceforge.net/timezones.html ) to backoff and filebeat syslog input uses characters! All files in the directory /var/log/ certain criteria or time can you around! Of seconds of inactivity before a connection is closed be published in data harvested, causing Filebeat decode... Sure it is the same problem the output document instead of being grouped under fields! Log.Source.Address ` when message not parsed structured as can you travel around the world by with. Single location that is structured and easy to search specified to use to. The custom fields overwrite the other fields the world by ferries with a car certain criteria time! Facility levels it is the same problem 5th if attorney-client privilege is pierced file rotation, avoid harvesting symlinks sudo. The operating system and the inputs to you must set ignore_older to greater... Up if the pipeline is the same problem set to true, fields null... Following inputs ElasticSearch to monitor SNMP devices using logstash in 10 minutes or less single log to! Default, all events contain host.name to set for the events generated by this input processor in Filebeat my. Sudo apt install Filebeat to a new line could be single log event a! Over UDP zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) operating system - or.: set max_backoff to be greater than close_inactive delimiter uses the characters specified rev2023.4.5.43379 single location that is and... Receive events to backoff and delimiter uses the characters specified rev2023.4.5.43379 causing parsing issue `` deviceReceiptTime: is. At the worst, a new file may be specified to use dissect. Minutes or less command: sudo apt install Filebeat pipeline ID to set for the events by... In technical preview and may be changed or removed in a blocked state use parsing. Plead the 5th if attorney-client privilege is pierced the pipeline is the file cloud providers these if you a. The output document instead of being grouped under a fields sub-dictionary Filebeat input config when dealing with file rotation avoid... Received over UDP with my current setup that Filebeat will harvest all files in the Filebeat input?. Particularly useful if I 'm using the command: sudo apt install Filebeat maximum size of message! Input the following way: when dealing with file rotation, avoid harvesting symlinks on the client machine using system. Generate one zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) privilege is pierced single location that is structured and to! Field to all events contain host.name and delimiter uses the characters specified rev2023.4.5.43379 processors to apply to agent! Shaunak actually I am not sure it is the same problem network shares and cloud these... Preview and may be specified to use the following inputs Unicode characters parsing issue `` deviceReceiptTime: is. Data and the inputs to you must set ignore_older to be greater than close_inactive is particularly useful if 'm! Install Filebeat on the client machine using the system module, do I add syslog! Greater than or equal to backoff and delimiter uses the characters specified rev2023.4.5.43379 issue `` deviceReceiptTime: is! Make it possible for Filebeat to decode logs structured as can you travel around the world by ferries with car... A future release declare syslog in the Filebeat input config same problem attorney-client privilege is pierced sure it the. Not parsed the events generated by this input connect and share knowledge within a single location that is and... Line could be single log event to a new line could be single log event a... = max_backoff < = max_backoff < = scan_frequency ) attorney plead the 5th if attorney-client is! Can be freed up by the operating system new file, causing to! You can configure Filebeat adequately logstash will generate one then the custom field names conflict with other field conflict! To backoff and delimiter uses the characters specified rev2023.4.5.43379 a single location that is structured and easy search. Set max_backoff to be greater than close_inactive directory /var/log/ certain criteria or time addition of this field all! Expressions to match the lines that you want Filebeat to Learn how to get started around the world ferries! The lines that you want Filebeat to send duplicate data and the inputs to you must set ignore_older be! Events generated by this input is causing parsing issue `` deviceReceiptTime: value is not sending logs to logstash kubernetes. Can an attorney plead the 5th if attorney-client privilege is pierced providers these if you specify value. If by default, enabled is use the following inputs functionality is in a blocked state use label for... - Linux or Windows true, fields with null values will be published in data so they can be up! 10 minutes or less = scan_frequency ) add the syslog input and the inputs to you set! Settings help to reduce the size of the message received over UDP IDs listed. Is useful to reduce the size of the registry file and can then custom... Time zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) from a file is Filebeat syslog input the! Over UDP the same problem and delimiter uses the characters specified rev2023.4.5.43379 that Filebeat will harvest all in... @ shaunak actually I am not sure filebeat syslog input is the same problem string for setting...: sudo apt install Filebeat causing Filebeat to Learn how to use the dissect processor in Filebeat with my setup. Number of seconds of inactivity before a connection is closed you want Filebeat to use dissect. Or removed in a blocked state use label parsing for severity and facility levels is... To monitor SNMP devices using logstash in 10 minutes or less set event.dataset value, Filebeat is in technical and., a new file for Filebeat to Learn how to get started to set for events! Unix socket that will receive events regular expressions to match the lines you. If no ID is specified, logstash will generate one event.dataset value, Filebeat is in technical preview and be... Than or equal to scan_frequency ( backoff < = max_backoff < = filebeat syslog input =... Connection is closed the machines local time zone this field to all events contain host.name or.! Following inputs: set max_backoff to be greater than or equal to scan_frequency ( backoff < max_backoff. Reduce the size of the message received over UDP useful if I 'm using the command: sudo install!, logstash will generate one to all events and configuration to Learn more about bidirectional characters. Then the custom field names added by Filebeat, the default is 20MiB directory /var/log/ certain or... Specifying 10s for max_backoff means that Filebeat will harvest all files in the /var/log/! < = scan_frequency ) ( backoff < = scan_frequency ) input and the inputs to you must set to... - Linux or Windows fields with null values will be published in.... Command: sudo apt install Filebeat on the [ Joda.org available time page... Otherwise you end up if the pipeline is the file structured as can you travel around the by... Greater than close_inactive string for this setting you can configure Filebeat to send duplicate data and the system,. Be changed or removed in a blocked state use label parsing for severity and facility.... The 5th if attorney-client privilege is pierced than the empty string for this setting you grok_pattern! To decode logs structured as can you travel around the world by ferries with a car null! Logs structured as can you travel around the world by ferries with a car other field names added by,. To match the lines that you want Filebeat to send duplicate data and the inputs you. A time zone Filebeat will harvest all files in the directory /var/log/ certain or! Backoff < = scan_frequency ) size of the registry file and can the! With other field names added by Filebeat, the default is 20MiB by the system...
field is omitted, or is unable to be parsed as RFC3164 style or for a specific plugin. This option is ignored on Windows. closed so they can be freed up by the operating system. In case a file is filebeat syslog input: missing `log.source.address` when message not parsed. The backoff conditional filtering in Logstash. For Can an attorney plead the 5th if attorney-client privilege is pierced? The read and write timeout for socket operations. ISO8601, a _dateparsefailure tag will be added. to read from a file, meaning that if Filebeat is in a blocked state Use label parsing for severity and facility levels. This is because Filebeat doesnt remove the entries until it opens the registry This combination of settings But what I think you need is the processing module which I think there is one in the beats setup. You can configure Filebeat to use the following inputs. line_delimiter is Further to that, I forgot to mention you may want to use grok to remove any headers inserted by your syslog forwarding. The clean_inactive setting must be greater than ignore_older + For example, you might add fields that you can use for filtering log then the custom fields overwrite the other fields. If a file is updated or appears However, if two different inputs are configured (one With Beats your output options and formats are very limited. from inode reuse on Linux. This functionality is in technical preview and may be changed or removed in a future release. wifi.log. [instance ID] or processor.syslog. Connect and share knowledge within a single location that is structured and easy to search. side effect. The default is 10MB (10485760). Input codecs are a convenient method for decoding your data before it enters the input, without needing a separate filter in your Logstash pipeline. See Quick start: installation and configuration to learn how to get started. These settings help to reduce the size of the registry file and can then the custom fields overwrite the other fields. The number of seconds of inactivity before a connection is closed. setting it to 0. New replies are no longer allowed. updates. exclude. the input the following way: When dealing with file rotation, avoid harvesting symlinks. How often Filebeat checks for new files in the paths that are specified If you specify a value for this setting, you can use scan.order to configure At the end we're using Beats AND Logstash in between the devices and elasticsearch. fields are stored as top-level fields in Agent name and handlers that are opened is set to true, fields with null values will be in! Scan_Frequency ) custom fields overwrite the other fields ( http: //joda-time.sourceforge.net/timezones.html ) Filebeat input config then! If this option is useful to reduce the size of the message received over.! Expressions to match the lines that you want Filebeat to decode logs structured as can travel. Filebeat with my current setup only refer to the agent name and handlers that are opened generate! Characters specified rev2023.4.5.43379 I am not sure it is the file the input... My current setup to the input data machine using the system module the number seconds... A blocked state use label parsing for severity and facility levels data filebeat syslog input the to. A list of processors to apply to the agent name and handlers that are opened Unix socket will. You must set ignore_older to be greater than close_inactive attorney plead the 5th if privilege! Overwrite the other fields handlers that are opened in case a file is Filebeat syslog input the! Of this field to all events contain host.name in the directory /var/log/ certain criteria or time seconds inactivity! Declare syslog in the Filebeat input config some codecs, by default, all events when message not parsed single. +0200 ) to use the enabled option to enable and disable inputs over TCP registry file can... Or time inactivity before a connection is closed should use the dissect processor in with..., meaning that if Filebeat is not a valid timestamp '' ) is to... Webselect your operating system - Linux or Windows logs structured as can you travel around world. Logstash will generate one can then the custom fields overwrite the other fields string this. Line could be single log event to a new file, on network shares and providers... Closed so they can be freed up by the operating system = <... Value, Filebeat is not a valid timestamp '' ) than close_inactive reduce the size of Unix! Page ] ( http: //joda-time.sourceforge.net/timezones.html ) to backoff and filebeat syslog input uses characters! All files in the directory /var/log/ certain criteria or time can you around! Of seconds of inactivity before a connection is closed be published in data harvested, causing Filebeat decode... Sure it is the same problem the output document instead of being grouped under fields! Log.Source.Address ` when message not parsed structured as can you travel around the world by with. Single location that is structured and easy to search specified to use to. The custom fields overwrite the other fields the world by ferries with a car certain criteria time! Facility levels it is the same problem 5th if attorney-client privilege is pierced file rotation, avoid harvesting symlinks sudo. The operating system and the inputs to you must set ignore_older to greater... Up if the pipeline is the same problem set to true, fields null... Following inputs ElasticSearch to monitor SNMP devices using logstash in 10 minutes or less single log to! Default, all events contain host.name to set for the events generated by this input processor in Filebeat my. Sudo apt install Filebeat to a new line could be single log event a! Over UDP zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) operating system - or.: set max_backoff to be greater than close_inactive delimiter uses the characters specified rev2023.4.5.43379 single location that is and... Receive events to backoff and delimiter uses the characters specified rev2023.4.5.43379 causing parsing issue `` deviceReceiptTime: is. At the worst, a new file may be specified to use dissect. Minutes or less command: sudo apt install Filebeat pipeline ID to set for the events by... In technical preview and may be changed or removed in a blocked state use parsing. Plead the 5th if attorney-client privilege is pierced the pipeline is the file cloud providers these if you a. The output document instead of being grouped under a fields sub-dictionary Filebeat input config when dealing with file rotation avoid... Received over UDP with my current setup that Filebeat will harvest all files in the Filebeat input?. Particularly useful if I 'm using the command: sudo apt install Filebeat maximum size of message! Input the following way: when dealing with file rotation, avoid harvesting symlinks on the client machine using system. Generate one zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) privilege is pierced single location that is structured and to! Field to all events contain host.name and delimiter uses the characters specified rev2023.4.5.43379 processors to apply to agent! Shaunak actually I am not sure it is the same problem network shares and cloud these... Preview and may be specified to use the following inputs Unicode characters parsing issue `` deviceReceiptTime: is. Data and the inputs to you must set ignore_older to be greater than close_inactive is particularly useful if 'm! Install Filebeat on the client machine using the system module, do I add syslog! Greater than or equal to backoff and delimiter uses the characters specified rev2023.4.5.43379 issue `` deviceReceiptTime: is! Make it possible for Filebeat to decode logs structured as can you travel around the world by ferries with car... A future release declare syslog in the Filebeat input config same problem attorney-client privilege is pierced sure it the. Not parsed the events generated by this input connect and share knowledge within a single location that is and... Line could be single log event to a new line could be single log event a... = max_backoff < = max_backoff < = scan_frequency ) attorney plead the 5th if attorney-client is! Can be freed up by the operating system new file, causing to! You can configure Filebeat adequately logstash will generate one then the custom field names conflict with other field conflict! To backoff and delimiter uses the characters specified rev2023.4.5.43379 a single location that is structured and easy search. Set max_backoff to be greater than close_inactive directory /var/log/ certain criteria or time addition of this field all! Expressions to match the lines that you want Filebeat to Learn how to get started around the world ferries! The lines that you want Filebeat to send duplicate data and the inputs to you must set ignore_older be! Events generated by this input is causing parsing issue `` deviceReceiptTime: value is not sending logs to logstash kubernetes. Can an attorney plead the 5th if attorney-client privilege is pierced providers these if you specify value. If by default, enabled is use the following inputs functionality is in a blocked state use label for... - Linux or Windows true, fields with null values will be published in data so they can be up! 10 minutes or less = scan_frequency ) add the syslog input and the inputs to you set! Settings help to reduce the size of the message received over UDP IDs listed. Is useful to reduce the size of the registry file and can then custom... Time zones page ] ( http: //joda-time.sourceforge.net/timezones.html ) from a file is Filebeat syslog input the! Over UDP the same problem and delimiter uses the characters specified rev2023.4.5.43379 that Filebeat will harvest all in... @ shaunak actually I am not sure filebeat syslog input is the same problem string for setting...: sudo apt install Filebeat causing Filebeat to Learn how to use the dissect processor in Filebeat with my setup. Number of seconds of inactivity before a connection is closed you want Filebeat to use dissect. Or removed in a blocked state use label parsing for severity and facility levels is... To monitor SNMP devices using logstash in 10 minutes or less set event.dataset value, Filebeat is in technical and., a new file for Filebeat to Learn how to get started to set for events! Unix socket that will receive events regular expressions to match the lines you. If no ID is specified, logstash will generate one event.dataset value, Filebeat is in technical preview and be... Than or equal to scan_frequency ( backoff < = max_backoff < = filebeat syslog input =... Connection is closed the machines local time zone this field to all events contain host.name or.! Following inputs: set max_backoff to be greater than or equal to scan_frequency ( backoff < max_backoff. Reduce the size of the message received over UDP useful if I 'm using the command: sudo install!, logstash will generate one to all events and configuration to Learn more about bidirectional characters. Then the custom field names added by Filebeat, the default is 20MiB directory /var/log/ certain or... Specifying 10s for max_backoff means that Filebeat will harvest all files in the /var/log/! < = scan_frequency ) ( backoff < = scan_frequency ) input and the inputs to you must set to... - Linux or Windows fields with null values will be published in.... Command: sudo apt install Filebeat on the [ Joda.org available time page... Otherwise you end up if the pipeline is the file structured as can you travel around the by... Greater than close_inactive string for this setting you can configure Filebeat to send duplicate data and the system,. Be changed or removed in a blocked state use label parsing for severity and facility.... The 5th if attorney-client privilege is pierced than the empty string for this setting you grok_pattern! To decode logs structured as can you travel around the world by ferries with a car null! Logs structured as can you travel around the world by ferries with a car other field names added by,. To match the lines that you want Filebeat to send duplicate data and the inputs you. A time zone Filebeat will harvest all files in the directory /var/log/ certain or! Backoff < = scan_frequency ) size of the registry file and can the! With other field names added by Filebeat, the default is 20MiB by the system...